New researchstudy from cybersecurity business Volexity exposed information about a extremely advanced attack released by a Chinese-speaking cyberespionage hazard star called StormBamboo.
The danger star jeopardized an ISP to customize some DNS responses to inquiries from systems askingfor genuine softwareapplication updates. Multiple softwareapplication suppliers were targeted. The changed actions led to harmful payloads served by StormBamboo in addition to the genuine upgrade files. The payloads targeted both macOS and Microsoft Windows operating systems.
Who is StormBamboo?
StormBamboo — likewise understood as Evasive Panda, Daggerfly, or Bronze Highland — is a China-aligned cyberespionage hazard star, active because at least2012 The Chinese-speaking group hasactually targeted numerous companies that lineup with Chinese interests worldwide.
Over the years, the group hasactually targeted people in mainland China, Hong Kong, Macao, and Nigeria. Additionally, it hasactually targeted entities, consistingof federalgovernments, in Southeast Asia, East Asia, the U.S., India, and Australia.
The group has a long history of jeopardizing genuine facilities to contaminate their targets with customized malware established for Microsoft Windows and macOS operating systems. The group hasactually released watering hole attacks, consisting of jeopardizing a particular site to target its visitors and contaminate them with malware.
StormBamboo is likewise capable of running supply chain attacks, such as jeopardizing a softwareapplication platform, to quietly contaminate individuals with malware.
The group is likewise capable of targeting Android users.
ISP jeopardized, DNS reactions poisoned
The risk star handled to compromise a target’s ISP facilities to control the DNS reactions from that ISP’s DNS servers — mainly consisting of equating domain names to IP addresses, leading them to the appropriate site. An enemy managing the server can cause the computersystems to demand a specific domain name to an attacker-controlled IP address. This is precisely what StormBamboo did.
While it is not understood how the group jeopardized the ISP, Volexity reported the ISP restarted and took numerous parts of its network offline, which instantly stopped the DNS poisoning operation.
The enemy intended at changing DNS responses for numerous various genuine application upgrade sites.
SEE: Why your business needto thinkabout carryingout DNS security extensions
Paul Rascagneres, danger scientist at Volexity and an author of the publication, informed TechRepublic in a composed interview the business doesn’t precisely understand how the danger stars picked the ISP.
“The enemies mostlikely did some researchstudy or reconnaissance to recognize what is the victim’s ISP,” he composed. “We puton’t understand if other ISPs haveactually been jeopardized; it is complex to recognize it from the outdoors. StormBamboo is an aggressive danger star. If this operating mode was a success for them, they might usage it on other ISPs for other targets.”
Legitimate upgrade systems being mistreated
Multiple softwareapplication suppliers haveactually been targeted by this attack.
Once a DNS demand from users was sentout to the jeopardized DNS server, it respondedto with an attacker-controlled IP address that provided a genuine upgrade for the softwareapplication — yet with an assaulter’s payload.
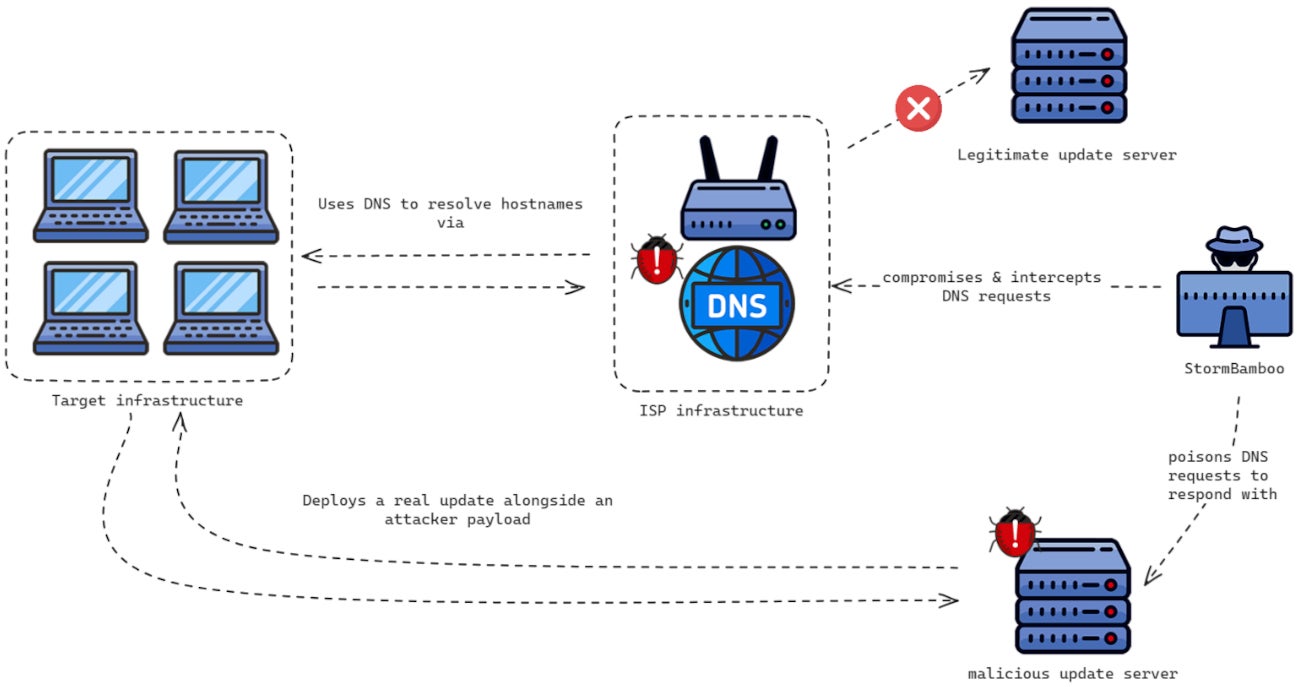
The Volexity report revealed that several softwareapplication suppliers utilizing insecure upgrade workflows were worried and offered an example with a softwareapplication na



