Blockchain security firm PeckShieldAlert reported a major hack involving Unleash Protocol, a decentralized platform built on Story Protocol, where an attacker drained around $3.9 million in user funds.
Here’s how the hack happened. PeckShieldAlert report revealed.
How the Unleash Protocol Hack Happened?
According to PeckShieldAlert, the attacker targeted Unleash Protocol’s multi-signature governance system.
By doing so, the attacker gained unauthorized admin access and pushed through a contract upgrade that had not been approved by the core team. This change opened the door for funds to be withdrawn directly from the protocol.
After withdrawing the funds, the attacker bridged the assets to Ethereum and began breaking them into smaller chunks.
On-chain data shows 1,337.1 ETH was deposited into Tornado Cash, a privacy tool often used to hide transaction trails.
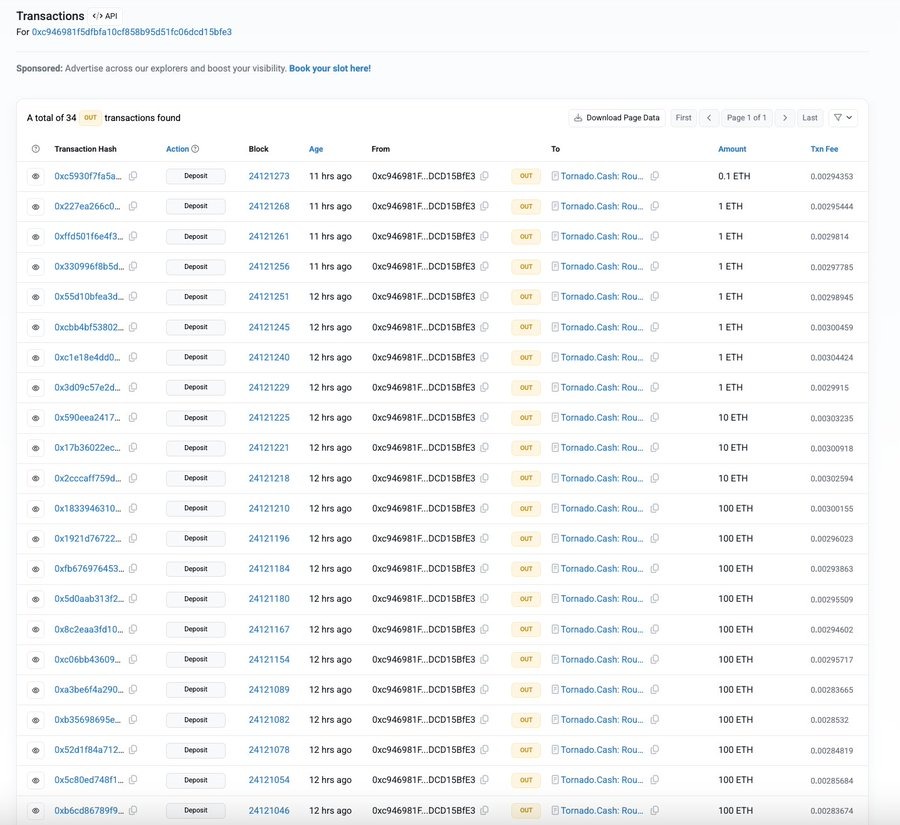
The repeated deposits, from small amounts to batches of 100 ETH, seem designed to hide the source of the stolen funds.
What Assets Were Affected in the Breach
In its official incident notice, Unleash Protocol confirmed that several assets were impacted during the exploit. These include WIP, USDC, WETH, stIP, and vIP. The team stressed that the withdrawals happened outside normal governance rules and were not approved internally.
Importantly, Unleash clarified that there is no evidence of any compromise to Story Protocol, its validators, or its core infrastructure. The issue appears limited strictly to Unleash-specific contracts and admin controls.
Following the discovery, Unleash Protocol immediately paused all operations to prevent further damage. The team is now working with independent security experts and forensic investigators to identify the root cause.
Users have been advised to avoid interacting with Unleash Protocol contracts until further updates are shared through official channels.
Never Miss a Beat in the Crypto World!
Stay ahead with breaking news, expert analysis, and real-time updates on the latest trends in Bitcoin, altcoins, DeFi, NFTs, and more.
FAQs
What caused the Unleash Protocol hack?
The hack happened after an attacker gained unauthorized admin control via the multi-signature system and p





